The Midnight Alert: How a Crypto Miner Hijacked My VPS and What I Did to Stop It
At 5 AM, my server hosting service sent an urgent alert: 100% CPU usage. What followed was a race to uncover a hidden crypto miner, a compromised Umami Analytics container, and a critical Next.js vulnerability. Here’s how I fought back—and how you can protect yourself.

It was 5:06 AM on December 6, 2025, when my phone lit up with a notification from my server hosting provider:
Your VPS plan has reached its CPU limit, which may cause your website or application to slow down, or even become temporarily unavailable.
I rubbed my eyes, assuming it was a false alarm. But when I logged into my dashboard, the CPU usage graph told a different story: a flat line at 100%, stretching back over an hour. My VPS, which usually idled at a quiet 4%, was now screaming under full load.
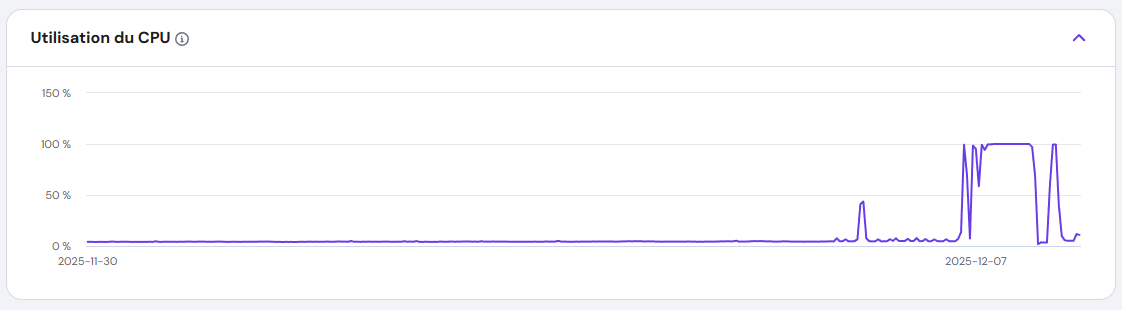
I hadn’t touched the server in days. No new deployments. No configuration changes. Something was wrong.
Everything else seemed OK from my point of view.
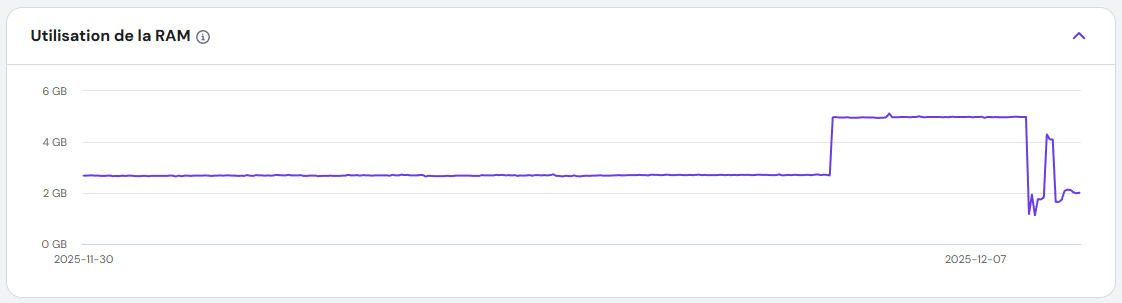
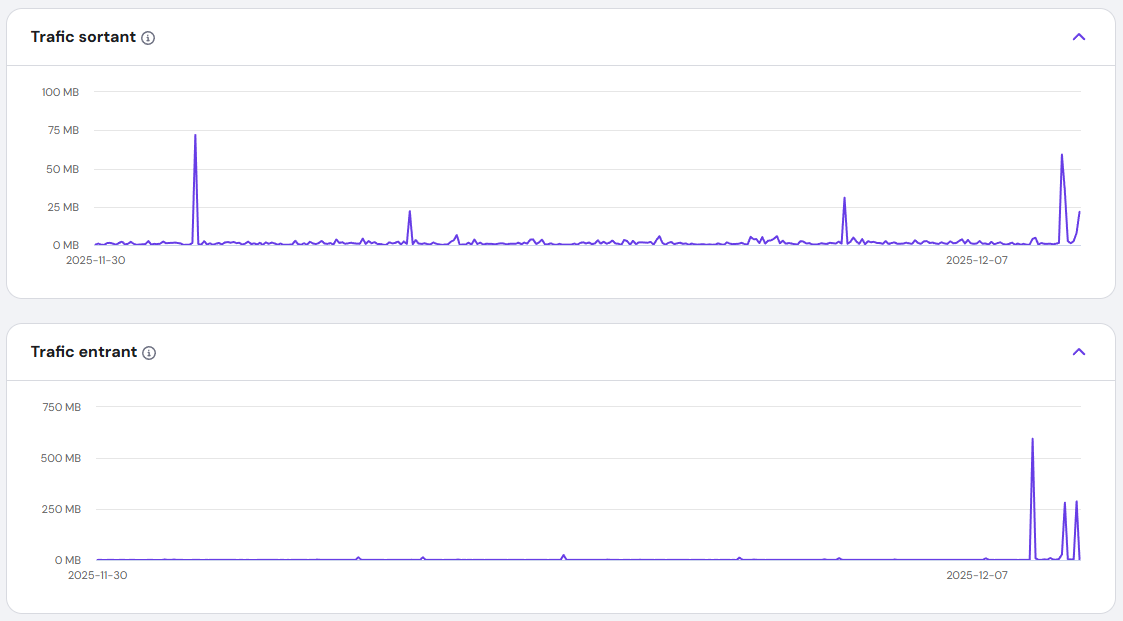
The Hunt for the Culprit: Stopping the Bleeding
First Suspicions: DDoS or a Runaway Process?
I ruled out a DDoS attack quickly—my traffic logs were normal. Next, I wondered if one of my applications had gone into an infinite loop. I restarted the VPS, but the problem persisted. The CPU usage remained stubbornly at 100%.
The Breakthrough: Umami Analytics
I run multiple Docker containers managed by Dokploy. One by one, I stopped each container, watching the CPU graph like a hawk. And then—success. When I stopped the Umami Analytics container, the CPU usage plummeted.
Umami? It’s just an analytics tool. Why was it suddenly consuming all my resources?
Uncovering the Malware: A Hidden Crypto Miner
The Virus Scan
I installed a virus scanner and let it run. Within minutes, it flagged a suspicious binary: fghfg, buried in a Docker volume. But the real shock came when I found apache.sh, a shell script connecting to https://tr.earn.top.I didn't know exactly what it was, but it knew it was not something good.
The Next.js Connection
The files were in a folder named Nextjs. That’s when it clicked. Earlier that week, I’d read about CVE-2025-55182 and CVE-2025-66478, a critical vulnerability in React Server Components. I checked the Umami Analytics GitHub repo and saw the confirmation: a recent patch for the compromised Next.js 15.3.1 dependency.
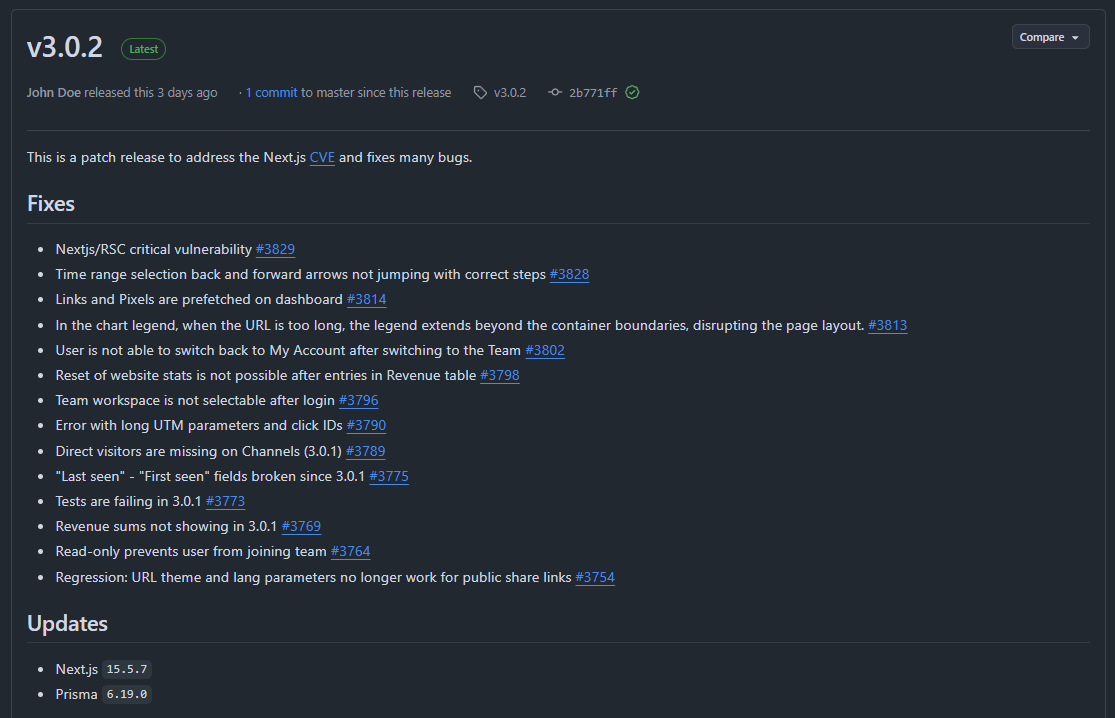
I was running Umami 2.18.1, which used the vulnerable version. The Next.js team’s official blog post confirmed my fears: attackers were exploiting this flaw to inject malicious code.

The Fix: Reclaiming My Server
Delete the Malware
I immediately deleted fghfg and apache.sh, but I knew the damage might run deeper.
Update and Rebuild
I pulled the latest Umami Analytics (3.0.2), which used the patched Next.js version. Then, I rebuilt the Docker container from scratch, ensuring no traces of the malware remained.
Watch the Recovery
I refreshed the CPU graph. The line dropped from 100% to normal levels within minutes. My VPS was finally breathing again.
The Bigger Lesson: Supply Chain Attacks in Node.js
This wasn’t just bad luck—it was a supply chain attack. Someone had exploited a vulnerability in a trusted library (Next.js) to turn my server into a crypto-mining slave. The scariest part? I never saw it coming.
Why This Matters
- Outdated dependencies are a ticking time bomb. Even one unpatched library can open the door to attackers.
- Docker volumes can hide malware. If you’re not scanning them, you might miss hidden threats.
- Supply chain attacks are rising. The Node.js ecosystem, with its vast dependencies, is a prime target.
How to Protect Yourself: Lessons from the Front Lines
Automate Updates
Set up automated dependency updates for your projects. Tools like npm audit and yarn audit can catch vulnerabilities before they become disasters.
Scan Your Containers
Use Trivy or Clair to scan Docker images for hidden threats. Don’t assume your containers are safe—verify it.
Monitor Relentlessly
CPU spikes? Unusual processes? Investigate immediately. Tools like Netdata or Prometheus can alert you before things spiral out of control.
Minimize Your Attack Surface
Use minimal base images for Docker. The fewer packages you have, the fewer opportunities for attackers.
Conclusion: A Wake-Up Call
That night, I learned a hard lesson: Security isn’t just about firewalls—it’s about vigilance. A single outdated dependency turned my VPS into a crypto-mining rig. But by acting fast—updating, scanning, and monitoring—I took back control.
While this was a serious cyber attack, there’s something oddly rewarding about facing such challenges. It forced me to dig deeper, learn more, and grow as a developer and sysadmin. Every problem is an opportunity to sharpen your skills, and this one reminded me just how important it is to stay proactive in the ever-evolving world of cybersecurity.
The digital world is full of hidden threats, but you don’t have to be a victim. Stay updated, stay alert, and never let your guard down. And remember: even the toughest challenges can become valuable lessons.







